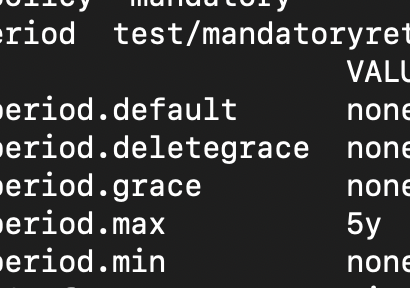
There is a really interesting tool to gather informations from a running process. Let´s assume a fellow admin is in her or his well-deserved vacation after a grueling release and now you have to reboot the new machine, because you have to service the memory. Of course you look into the documentation and you find a process that isn´t covered by the documentation and there doesn´t seem to be an startup script or SMF manifest that starts this application. D’oh … yet another last-minute pre-vacation change … shouldn’t happen, but it does happen from time to time. I used it as one of the tools in my tool belt to find out if really everything has persisted into start up files and documentation.1
Let´s assume you found an process called application.py in the process list:
root@testbed:~# pargs -e 3865
3865: /usr/bin/python ./application.py --db=testdb --username=test
envp[0]: SHELL=/usr/bin/bash
envp[1]: DB_PASSWORD=narf
envp[2]: LC_MONETARY=
(...)
envp[17]: MAIL=/var/mail/root
envp[18]: LC_NUMERIC=
envp[19]: _=/usr/bin/nohupThere is another interesting switch. You can use pargs with the -l switch to get the full command line that was used to start the script
root@testbed:~# pargs -l 3865
/usr/bin/python ./application.py '--db=testdb' '--username=test'-
Okay, the last test is simply rebooting the system at the end and look if everything still works, but i like this test reboot as drama free as possible. ↩